Research Thrusts
Thrust 1:
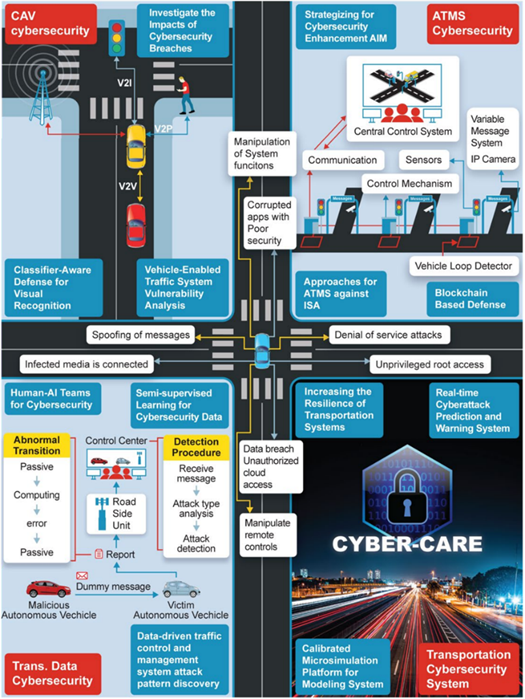
Connected and Automated Vehicle (CAV) Cybersecurity research is a key component of the USDOT Intelligent Transportation Systems (ITS) research program. CYBER-CARE’s efforts shall address complex questions of ensuring future CAV safety in cyber environments:
- Is it possible to use location to determine whether the information provided by a vehicle is reliable?
- All messages received from various devices require validation, so how can scalability be improved when the number of devices/nodes increases?
- How can cyberattacks that result in accidents due to a breakdown of the internal software be detected and avoided?
Thrust 2:
AI Application and Transportation Data Security - Given the key role of data in transportation communications with inadequate cybersecurity detection, CYBER-CARE will address the challenging problem of identifying cyberattacks via big data analysis by looking at a couple of manageable sub-problems:
- How can cyberattacks against an open network or system that aim to compromise information or disable devices for personal gain be avoided?
- How can hackers be detected and prevented from gaining access to connected vehicles to steal money or personal information or compromise systems?
- Which identity and privacy metadata will be shared with unknown transportation participants in a cybersecurity incident?
Thrust 3:
Advanced Traffic Management System (ATMS) Cybersecurity - In highly dynamic, wide-area traffic scenarios, e.g., in Advanced Traffic Management System (ATMS), centralized communication frameworks are insufficient. CYBER-CARE will develop a decentralized communication framework and future transportation solutions to ensure participants’ security and safety by addressing the following needs:
- Conflicts must be governed without rolling back to a centralized framework, so who should manage conflicts when all nodes are assumed to have similar rights?
- If each node in a decentralized framework is distinct (e.g., a key validation, communication, or data storage node, creating more vulnerability), how to protect multiple attack surfaces?
- How to optimize the process of data storage through sensors and in-vehicle cellular
vehicle-to-everything (V2X) components?
Thrust 4:
Next-Generation Transportation Cybersecurity Systems - Protecting next-generation transportation cybersecurity systems is complicated due to their reliance on multiple sub-systems, including sensors, weather stations, and smart vehicle networks. CYBER-CARE will address this problem and create reliable, next-generation transportation cybersecurity systems in various ways:
- What are the appropriate models for evaluating the resilience of these systems against cybersecurity attacks on one or more sub-systems?
- How to use the proposed models to discover optimal attacks over a combinatorial space of possible attacks?
- In the case of the simultaneous occurrence of extreme events (e.g., power outages and hurricanes), what are critical components for increasing system resilience?